Search for "29789" returned 150 results

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

63 min
Through a PRISM, Darkly
Everything we know about NSA spying

60 min
Windows drivers attack surface
some 'new' insights

63 min
Building Custom Pinball Machines
What you need and how it works. An experiences report

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
60 min
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…

57 min
“I feel like a criminal and I have to be god at the same time”
Perceptions of hackers and hacktivists on their…

61 min
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…
115 min
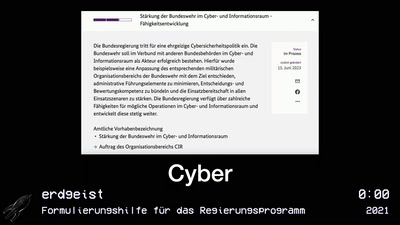
Vierjahresrückblick des CCC
Nix los und viel zu tun
77 min
Entbehrliches
Unterhaltsames Wissen aus der Wikipedia

113 min