Search for "Shane" returned 1298 results

61 min
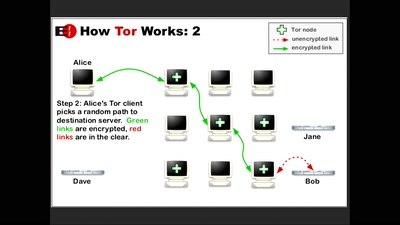
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
46 min
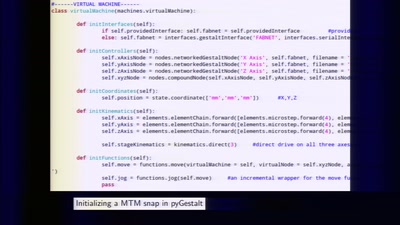
Making machines that make
rapid prototyping of digital fabrication and…

51 min
How to contribute to make open hardware happen
Mooltipass, Openpandora/Pyra and Novena/Senoko: how I…
55 min
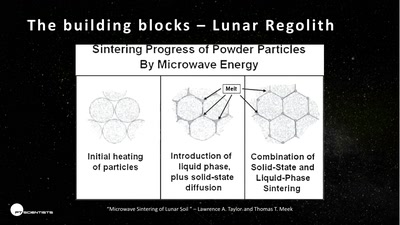
3D printing on the moon
The future of space exploration

60 min
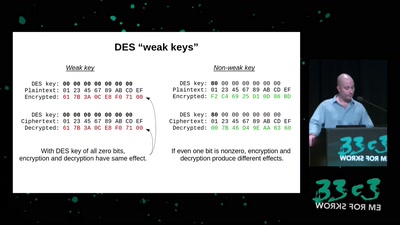
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

60 min
Are machines feminine?
exploring the relations between design and perception of…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

45 min
To Protect And Infect
The militarization of the Internet

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

58 min