Search for "535" returned 2058 results

62 min
Kyber and Post-Quantum Crypto
How does it work?

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time
26 min
Plants & Machines
Food replicating Robots from Open Source Technologies

44 min
Open Code Verlesung
Lesung des öffentlichen Sourcecodes
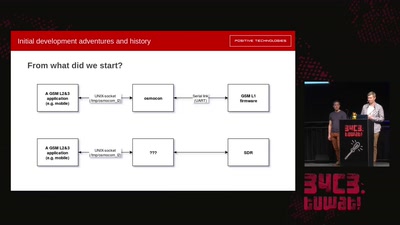
31 min
Running GSM mobile phone on SDR
SDR PHY for OsmocomBB

28 min
Home Distilling
Theory and practice of moonshining and legal distilling

26 min
Hacking the World
The struggle for security for all.

30 min
On Computing Numbers, with an Application to Problems of our Society
Journalism ♥ Computer Science

32 min