Search for "31c3" returned 2410 results

60 min
Mein Bot, der Kombattant
Operative Kommunikation im digitalen Informationskrieg

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption
61 min
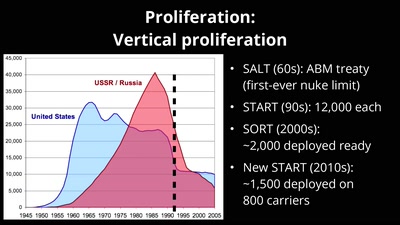
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…

30 min
Privacy and Consumer Markets
Reversing the Surveillance Business Model

25 min
»Hard Drive Punch«
Destroying data as a performative act

39 min
The automobile as massive data gathering source and the consequences for individual…
The next big privacy heist

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

33 min
IFG – Mit freundlichen Grüßen
Neue Energie für die Informationsfreiheit

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP
67 min
Mit Kunst die Gesellschaft hacken
Das Zentrum für politische Schönheit

60 min
SS7: Locate. Track. Manipulate.
You have a tracking device in your pocket

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

32 min