Search for "rEJl" returned 1474 results

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
59 min
How to build a submarine and survive
Wie wir mit begrenzten Mitteln ein U-Boot gebaut haben und…
30 min
Automatically Subtitling the C3
How speech processing helps the CCC subtitle project, and…

28 min
Long war tactics
or how we learned to stop worrying and love the NSA
62 min
Internet, the Business Side
a try to explain the ecosystem

62 min
radare demystified
after 1.0

55 min
3D Casting Aluminum
Too Much Fun with Microwaves

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology
38 min
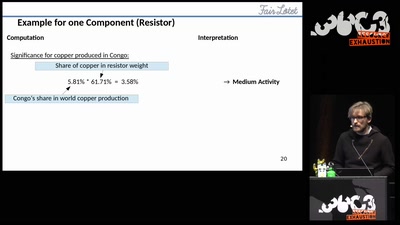
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…

40 min
Psychedelic Medicine - Hacking Psychiatry?!
Psychedelic Therapy as a fundamentally new approach to…
35 min
Wallet Security
How (not) to protect private keys

61 min