Search for "Udo Vetter" returned 1154 results

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
32 min
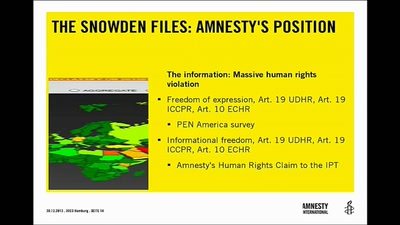
Human Rights and Technology
"A New Hope" or "The Empire Strikes Back"?

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux
32 min
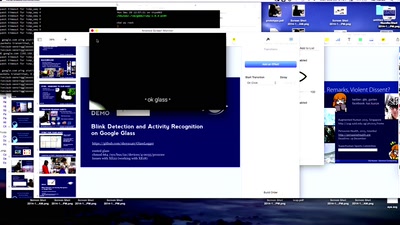
Eye Wear Computing
Augmenting the Human Mind

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…

60 min
Quantum Cryptography
from key distribution to position-based cryptography
32 min
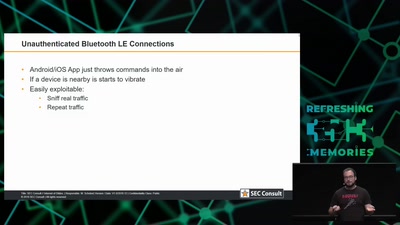
Internet of Dongs
A long way to a vibrant future

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

38 min
Zapfenstreich
Über Algorithmen im Krieg, aber was hat die Kunst damit…

33 min
Open source experimental incubator build up
call for participation in project and product development
46 min
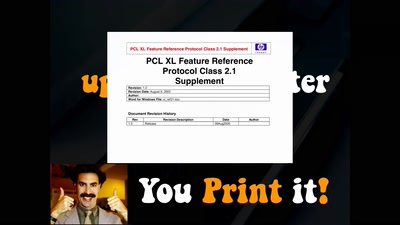
What The Fax?!
Hacking your network likes it's 1980 again

61 min
QualityLand
Lesung

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
50 min
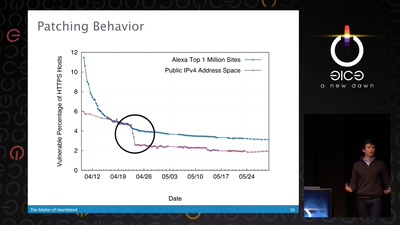
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…
36 min