Search for "Lisa" returned 984 results

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.
62 min
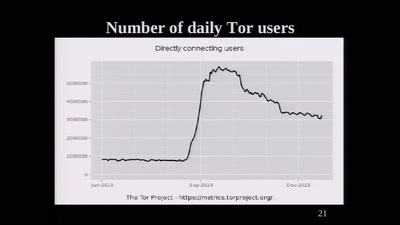
The Tor Network
We're living in interesting times
56 min
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

50 min
The eXperimental Robot Project
An open-hardware bipedal walking machine

65 min
Mind-Hacking mit Psychedelika
Eine Einführung in die Wirkungsweise psychedelischer…

51 min
Funky File Formats
Advanced binary tricks

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster
99 min
Fnord-Jahresrückblick
Wir helfen euch, die Fnords zu sehen!

126 min
Logbuch:Netzpolitik 466
Die Ibiza-Affäre und ihre Folgen
58 min
Hacking how we see
A way to fix lazy eye?

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

55 min