Search for "m-1-k-3" returned 9406 results

59 min
State of Emergent Democracy
Where are we today?

58 min
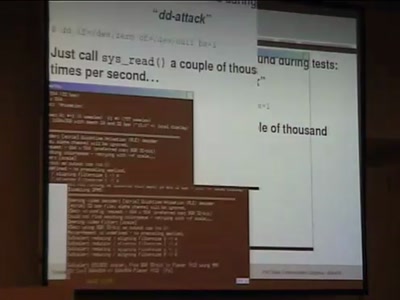
Physical Security
The Good, the Bad and the Ugly

105 min
Fight for your Right to Fileshare
Content Flatrate, not Copyright War

115 min
Passive covert channels in the Linux kernel
Implementation and detection of kernel based backdoors and…

117 min
Honeypot Forensics
No stone unturned or: logs, what logs?

45 min
The Convergence of Anti-Counterfeiting and Computer Security
Reverse-engineering currency detection systems

43 min
Pirate Radio
Running a Station and Staying on the Air
34 min