Search for "Twi"
prev
next

64 min
Details about the man hunt for Julian Assange and Wikileaks
61 min
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

31 min
Things you always wanted to know about NIC drivers
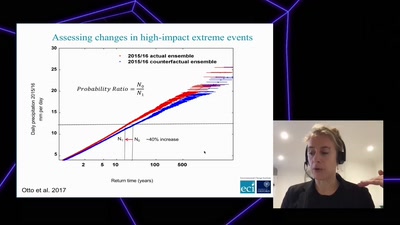
58 min
How human-induced climate change affects weather (& how we…

33 min
Reports from the Frontlines

39 min
When your browser is mining coins for other people

39 min
Spoiler: Apple is bad at patching
31 min
From war pigeons in 1914 to cyborg moths in 2014

57 min
Conservation Genomics between Taxonomy, Big Data,…

33 min
Dark Matter and Gravitational Waves
38 min
Aarch64 binary rewriting adventures but mostly pains

33 min
call for participation in project and product development
39 min
Egypt's Civil Society Under Attack

31 min
Hijacking debug components for embedded security

56 min
what is the winning move?

69 min
How to make your own telescope

55 min
Turning copyright upside-down with metadata

60 min
How Betrusted Aims to Close the Hardware TOCTOU Gap

55 min
The role of social-graphs for Drones in the War on Terror.
prev
next








