Search for "575" returned 1900 results

49 min
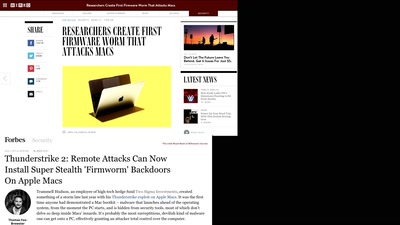
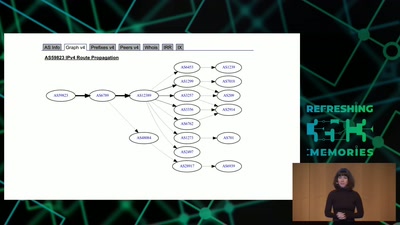
BREACH in Agda
Security notions, proofs and attacks using dependently…

47 min
Ein kurzer Blick in .git/
Ich gebe einen Überblick über die Ideen hinter git und die…
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…
40 min
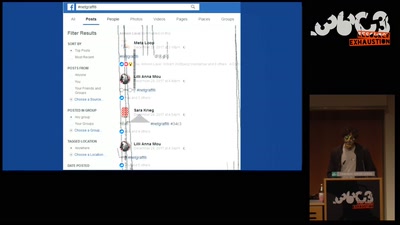
Art against Facebook
Graffiti in the ruins of the feed and the…
26 min
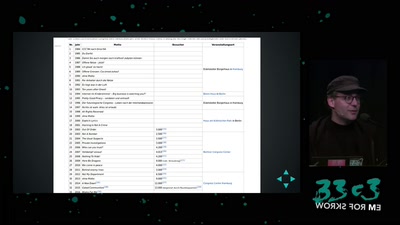
Der 33 Jahrerückblick
Technology and Politics in Congress Talks, from 1984 to now
42 min
Domain Name System
Hierarchical decentralized naming system used since 30 years
60 min
Netzpolitik in der Schweiz
NDG, BÜPF und wie wir uns dagegen wehren
59 min
The Surveillance State limited by acts of courage and conscience
An update on the fate of the Snowden Refugees
56 min
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform
61 min
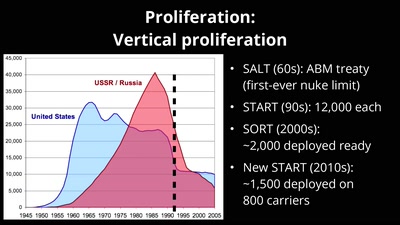
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

60 min
Quantum Cryptography
from key distribution to position-based cryptography

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

59 min
Security of the IC Backside
The future of IC analysis

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

46 min