Search for "overflo" returned 135 results

51 min
How to drift with any car
(without your mom yelling at you)

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…
59 min
The Ultimate SPC700 Talk
The hardware behind the music of Super Mario World, Chrono…
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…
54 min
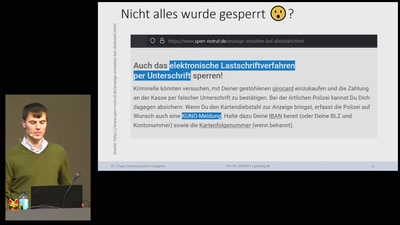
Oh no: KUNO - Gesperrte Girocards entsperren
Über „Girodays“ & anderen Kuriositäten
46 min
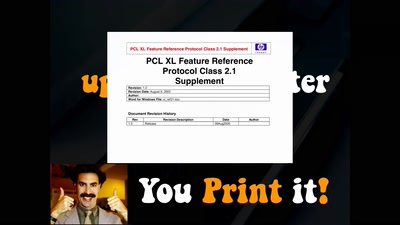
What The Fax?!
Hacking your network likes it's 1980 again

31 min
TrustZone is not enough
Hijacking debug components for embedded security
56 min
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform

49 min
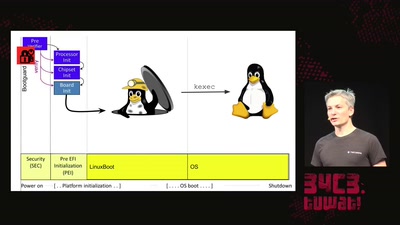
Open Source Firmware
Eine Liebesgeschichte

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

56 min
Viva la Vita Vida
Hacking the most secure handheld console
43 min
The Mars Rover On-board Computer
How Curiosity's Onboard Computer works, and what you can…

56 min


![Wie man zu[mr] System Ingenieur(in)? wird](https://static.media.ccc.de/media/events/rc3/133-ed57ba19-7686-55a9-b228-38c5a10b444b.jpg)