Search for "fake" returned 2875 results

57 min
Make Wi-Fi fast again
Eine kleine Einführung in den 802.11ac Standard
55 min
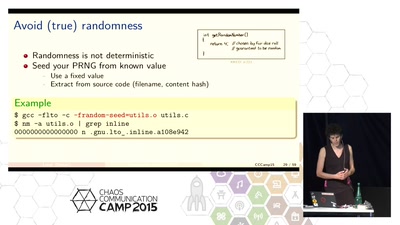
How to make your software build reproducibly
Get a verifiable path from source to binary

119 min
CR208 - How to make a Congress
Ein Blick hinter die Kulissen

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

38 min
Content take-downs: Who cleans the internet?
EU plans to swipe our freedom of expression under the carpet
26 min
Make the web more fair and social
Using decentralized tools

69 min
Bang! or how to make a demo
"Use your faults, use your defects, then your're gonna be a…

42 min
Shut up, do research and take our money!
Chaotische Catalysator Stipendien (CCS) wird zwei Jahre…
30 min
What can AI learn from your face?
The making of HowNormalAmI.eu
51 min
Make Your Tech and Wear It Too
Stories from an e-textile tailor

30 min