Search for "ar3itrary"
prev
next
58 min
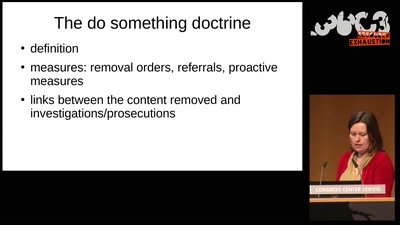
A rough guide to over-regulating free speech with…

51 min
An AES encrypted radio system

54 min
Unlocking God Mode on Linux

42 min
Real-world exploits and mitigations in Large Language Model…

60 min
Making it easier to avoid low-level compromise, and why…

46 min
Exploring a new attack surface on the 3DS
62 min
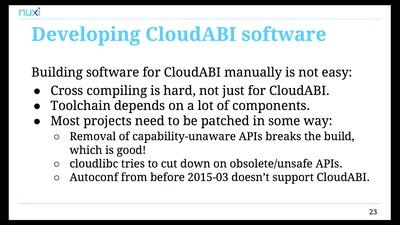
Pure capability-based security for UNIX
43 min
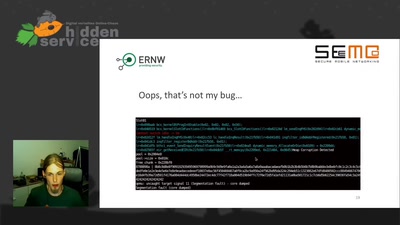
It is just a broken memcpy in the Bluetooth stack. Do we…

32 min
Math, Functional Programming, Theorem Proving, and an…
52 min
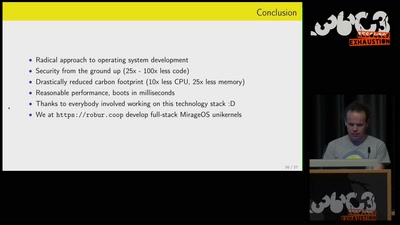
Reducing carbon footprint of network services with MirageOS…

58 min
weaknesses in the encryption of solid state drives (SSDs)
66 min
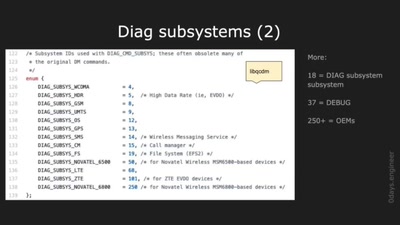
Harnessing diagnostics for baseband vulnerability research
62 min
Evolve your hack into robust software!
prev
next









