Search for "HItc" returned 389 results

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
59 min
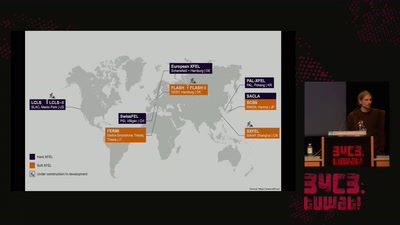
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

63 min
Traue keinem Scan, den du nicht selbst gefälscht hast
"Bei Kopierern kommt das raus, was man reinsteckt." – Wer…
56 min
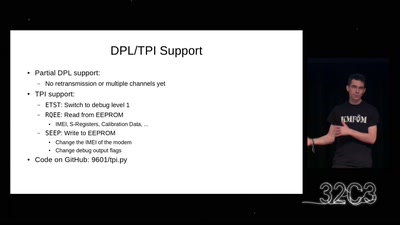
Iridium Update
more than just pagers

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

44 min
ASLR on the line
Practical cache attacks on the MMU

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs

69 min