Search for "Twi"
prev
next

40 min
Call the frontdoor to install your backdoors

63 min
Moving Beyond Single Points of Failure for Software…

41 min
A Dive into Reverse Engineering and Understanding the iPod…
56 min
PART II: disrupting disruption

49 min
Activity Recognition for the Mind

60 min
How not to do DOCSIS networks
36 min
A deep dive into an underrepresented research area
38 min
A gentle introduction to place & route algorithms for…

46 min
An introduction and critique of the EC proposal for a…

53 min
Social media break up coordinator

60 min
Making it easier to avoid low-level compromise, and why…

60 min
Fun and frightening uses of always-on camera enabled…

42 min
Real-world exploits and mitigations in Large Language Model…
57 min
How to make art after Snowden?

64 min
post-existentialism is the question, not post-privacy
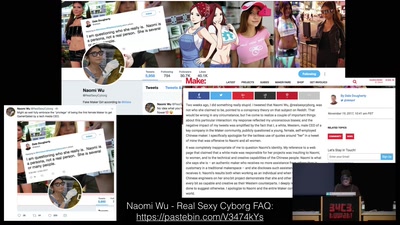
56 min
Obsolete Technologies + Critical Material Studies in Media…

53 min
About military RF communication surveillance and other…
prev
next








