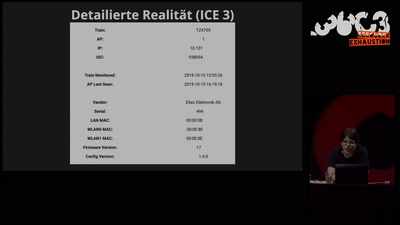
Search for "934" returned 1892 results

60 min
Hacking Reality
Mixed Reality and multi-sensory communication
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…

60 min
Are machines feminine?
exploring the relations between design and perception of…

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

62 min
„Wir beteiligen uns aktiv an den Diskussionen“
Die digitale „Agenda“ der Bundesregierung aus inhaltlicher,…

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

16 min
Youth Hacking 4 Freedom
Hacking competition for teenagers from Europe

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!

17 min
c3 MorningShow
Tag 4

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…
62 min
Internet, the Business Side
a try to explain the ecosystem

57 min