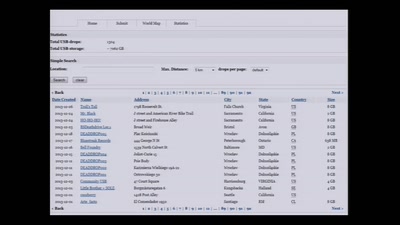
Search for "566" returned 1923 results

58 min
Virtual Machine Introspection
From the Outside Looking In

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…
61 min
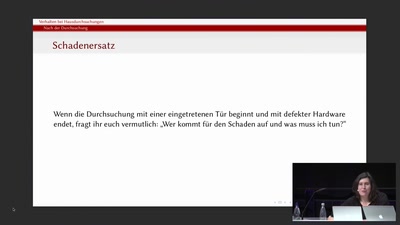
Verhalten bei Hausdurchsuchungen
Praktische Hinweise für den Kontakt mit der Staatsmacht
57 min
Hello World!
How to make art after Snowden?

58 min
Die Krise der Bilder ist die Krise der Politik
Die Krise der Politik ist die Krise der Bilder

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

69 min
Telescope Making
How to make your own telescope

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

33 min
Retail Surveillance / Retail Countersurveillance
50 most unwanted retail surveillance technologies / 50 most…
54 min
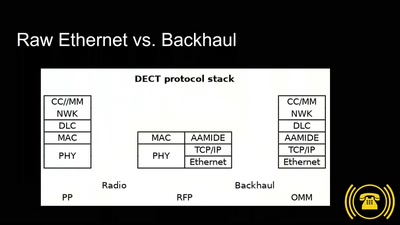
#mifail oder: Mit Gigaset wäre das nicht passiert!
DECT is korrekt.

61 min
Die göttliche Informatik
Die Informatik löst formale (mathematisch modellierte)…
59 min
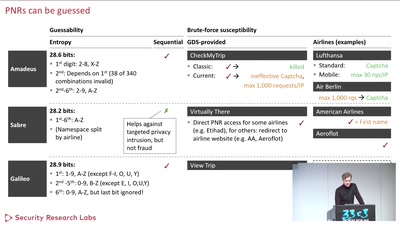
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…
61 min
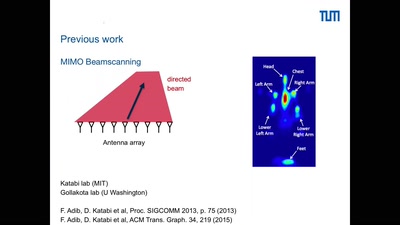
Holography of Wi-Fi radiation
Can we see the stray radiation of wireless devices? And…
61 min
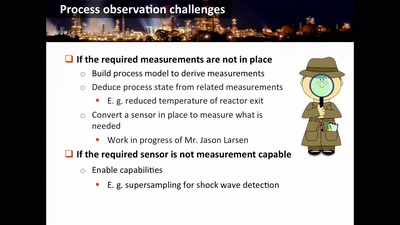
Damn Vulnerable Chemical Process
Exploitation in a new media

58 min