Search for "andi" returned 7269 results
53 min
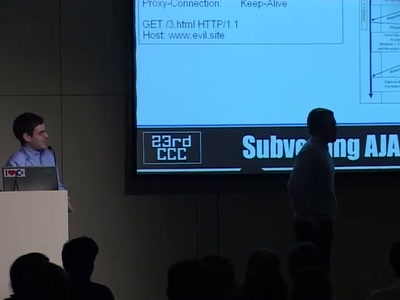
Subverting AJAX
Next generation vulnerabilities in 2.0 Web Applications

63 min
Counter-Development
The Accessibility of Technology as an Addendum to…

56 min
Corp vs. Corp
Profiling Modern Espionage
26 min
Julian’s Paper Craft (JPC) und 4D-Printing
A New Way of Bending Space
60 min
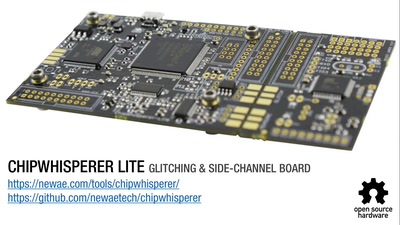
Opening Closed Systems with GlitchKit
'Liberating' Firmware from Closed Devices with Open Source…

50 min
Remote work in Corona times
Everything changes, everything remains the same
38 min
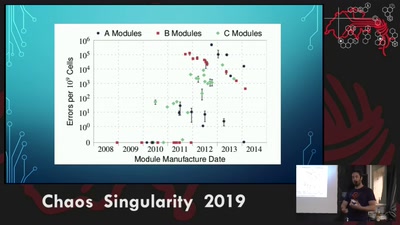
Rowhammer exploit
Viability of the Rowhammer Attack when ECC memory is used
61 min