Search for "Remote" returned 1056 results
59 min
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

66 min
The Snowden Refugees under Surveillance in Hong Kong
A Rapidly Emerging Police State and Imminent Deportation to…

46 min
Writing secure software
using my blog as example
41 min
SCADA StrangeLove 2
We already know
37 min
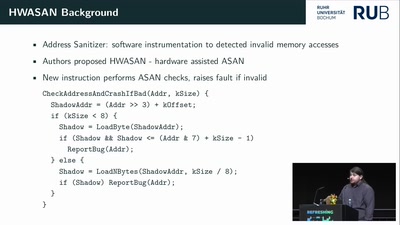
Inside the AMD Microcode ROM
(Ab)Using AMD Microcode for fun and security

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures
47 min
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…
58 min
Operation Triangulation
What You Get When Attack iPhones of Researchers

41 min
Ten Years of Rowhammer:
A Retrospect (and Path to the Future)
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways
58 min
Firebird Open Source Database Quick Start
Why Firebird is a powerful alternative database system
47 min
All cops are broadcasting
Obtaining the secret TETRA primitives after decades in the…

25 min