Search for "Udo Vetter" returned 1123 results
59 min
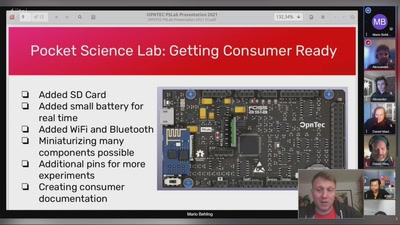
Top X* usability obstacles
*(will be specified later based on usability test with…

58 min
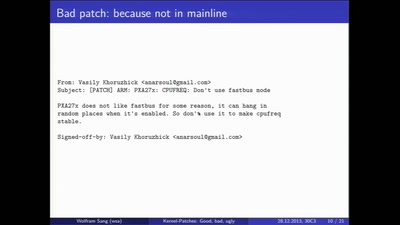
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
39 min
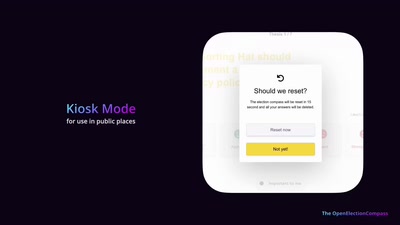
Should e-voting experience of Estonia be copied?
Observer report of 2023 parliamentary elections

33 min
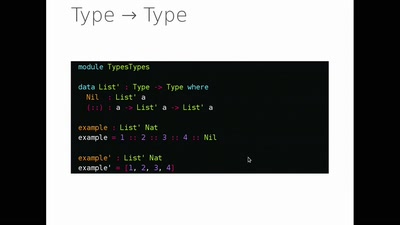
Turing Complete User
What can be done to protect the term, the notion and the…

34 min
Scuttlebutt
The decentralized P2P gossip protocol

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

63 min
Building Custom Pinball Machines
What you need and how it works. An experiences report

30 min
apertus° AXIOM
The first Open Source Cinema Camera

64 min
Magic Lantern
Free Software on Your Camera
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways

40 min
A year of surveillance in France: a short satirical tale by La Quadrature du Net
From the so-called Country of human rights to a…

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…

30 min