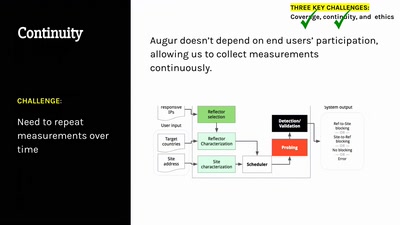
Search for "robot" returned 535 results

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom
45 min
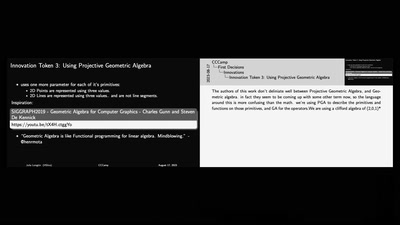
A geometry engine from first principles
the first three years of a six month project.
38 min
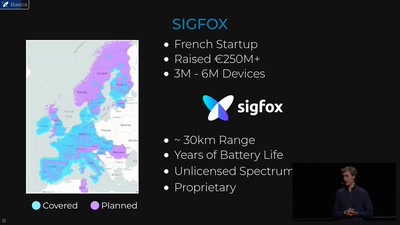
Hunting the Sigfox: Wireless IoT Network Security
Dissecting the radio protocol of Sigfox, the global…

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox
47 min
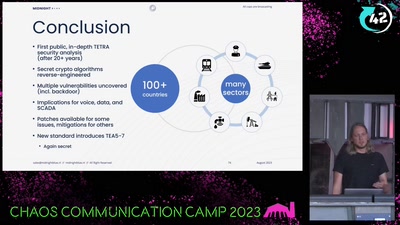
All cops are broadcasting
Obtaining the secret TETRA primitives after decades in the…
31 min
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…
66 min
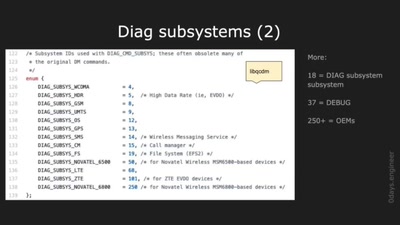
Advanced Hexagon Diag
Harnessing diagnostics for baseband vulnerability research

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

46 min
CounterStrike
Lawful Interception

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

41 min