Search for "ty5E" returned 708 results

37 min
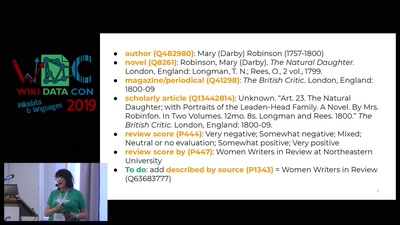
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux
35 min
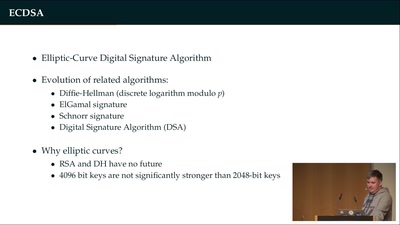
Wallet Security
How (not) to protect private keys
39 min
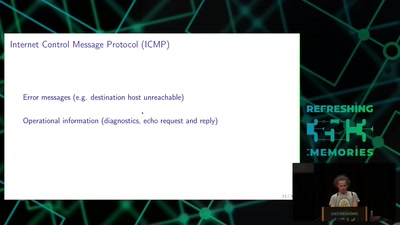
Transmission Control Protocol
TCP/IP basics
35 min
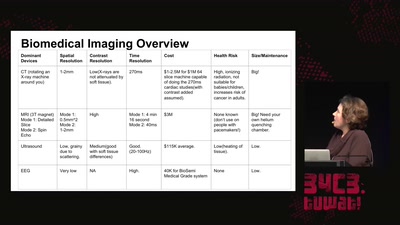
Low Cost Non-Invasive Biomedical Imaging
An Open Electrical Impedance Tomography Project
47 min
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish
61 min
Grow your own planet
How simulations help us understand the Universe

45 min
To Protect And Infect
The militarization of the Internet

63 min
goto fail;
exploring two decades of transport layer insecurity

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
60 min