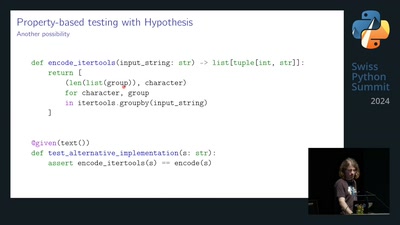
Search for "ths" returned 8600 results

49 min
Mining Search Queries
How to discover additional knowledge in the AOL query logs

76 min
Information Operations
Sector-Oriented Analysis of the Potential Impact and…
65 min
eVoting after Nedap and Digital Pen
Why cryptography might not fix the issue of transparent…

61 min
Defend your Freedoms Online: It's Political, Stupid!
A Positive agenda against the next ACTA, SOPA, and such

59 min
Vulnerability markets
What is the economic value of a zero-day exploit?

53 min
Know your compiler
...and what the optimizer does so you don't have to
28 min
Accelerating Scientific Research through Spinning Out a Software Company
Our story about finding the balance between free and…

48 min
TASBot OoT ACE:
How to get the Triforce on an N64 via controller input

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

59 min
Paranoid Machines
threads of symptom and haunting woven throughout the…

56 min
We are all lawmakers!
How to further transparency by law – the Hamburg example…

65 min
Building an international movement: hackerspaces.org
What we did so far. What will happen in the future.

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…
36 min
Is my system fast?
An introduction of some tools that help to answer this…

49 min
Syscall proxying fun and applications
Introduction to syscall proxying and applications for in…

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

59 min
Provable Security
How I learned to stop worrying and love the backdoor

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…

37 min
Decentralized clustering
Making the net - even if your local dicators hate it!
47 min
Test-Driven Web Development
Treating your web application like the grown-up it is

45 min