Search for "big data"
prev
next
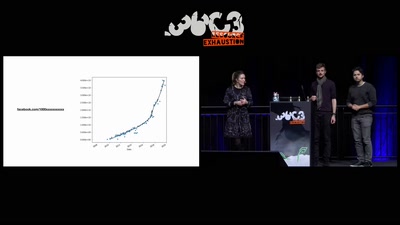
60 min
How thousands of Facebook, You Tube and Instagram pages…

40 min
Techniques - Tools - Tricks

58 min
CITL: Quantitative, Comparable Software Risk Reporting
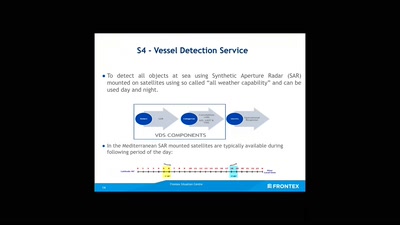
40 min
How an agency implements Fortress Europe by degrading…
58 min
A survey of BSD kernel vulnerabilities.

57 min
A demystification of the exploit development lifecycle

58 min
Intimiditation surveillance and other tactics observed and…
62 min
Auditing Boot Loaders by Example
36 min
A deep dive into an underrepresented research area

64 min
Dissecting a Modern Wireless Network for the Internet of…

40 min
From the so-called Country of human rights to a…

58 min
Possible paths from today's ghastly hackery to what…
prev
next








