Search for "125" returned 2619 results
63 min
This Is Not A Game
Eine kurze Geschichte von Q als Mindfuck-Spiel

55 min
Fuzzing the phone in the iPhone
D-d-d-di-di-d-d-di-d-di-d-di-d-dimm!

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

34 min
Snowden Effect vs. Privacy Paradox
Einstellungen und Internetnutzungsverhalten im Kontext des…
39 min
Why do we need an open food information platform
We want all data about food to be linked and public

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology
40 min
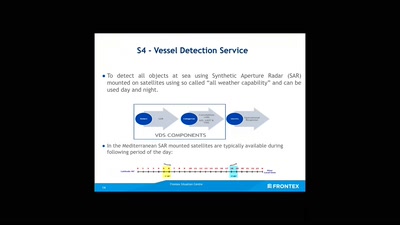
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…

63 min
Analyze the Facebook algorithm and reclaim data sovereignty
Algorithms define your priorities. Who else besides you can…
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators

41 min
MicroPython – Python for Microcontrollers
How high-level scripting languages make your hardware…
63 min
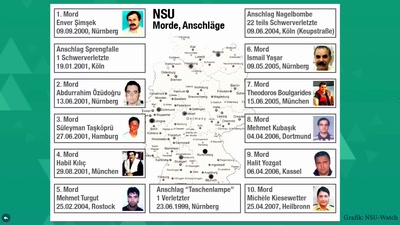
"Das ist mir nicht erinnerlich." − Der NSU-Komplex heute
Fünf Monate nach dem Urteil im ersten NSU-Prozess

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

54 min
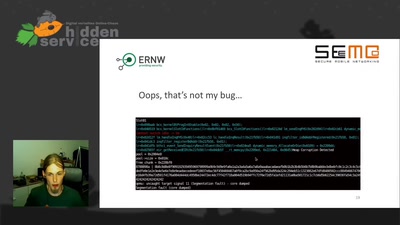
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox
43 min
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

32 min
History and implications of DRM
From tractors to Web standards
31 min
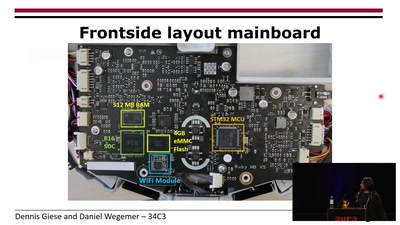
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

32 min