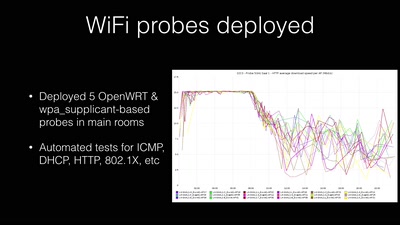
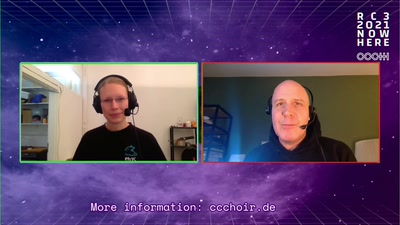
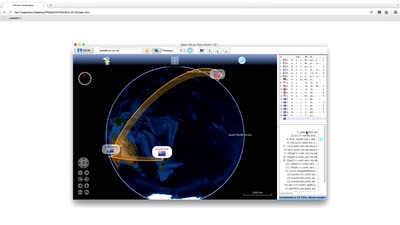
Search for "51" returned 3735 results

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age
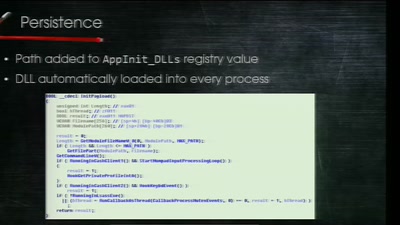
56 min
Electronic Bank Robberies
Stealing Money from ATMs with Malware

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…
60 min
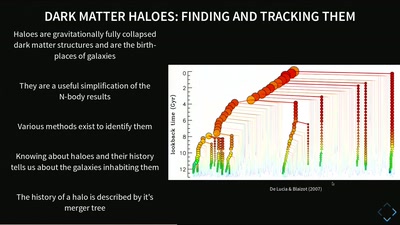
Simulating Universes
What Virtual Universes Can Tell Us About Our Own

60 min
Lets break modern binary code obfuscation
A semantics based approach

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy
42 min
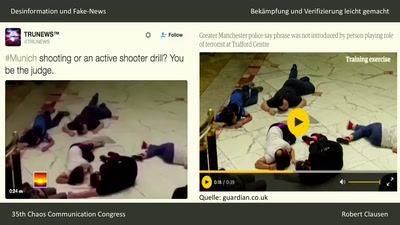
Desinformation und Fake News
Bekämpfung und Verifizierung leicht gemacht
60 min
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

62 min
radare demystified
after 1.0

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…
61 min
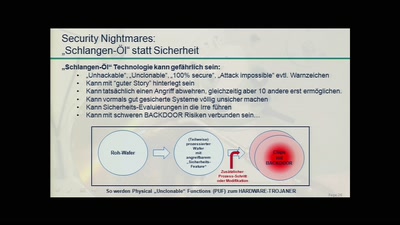
25 Jahre Chipkarten-Angriffe
Von der Historie zur Zukunft

62 min
Deine Rechte sind in diesen Freihandelsabkommen nicht verfügbar
Der Protest gegen TTIP und CETA

61 min