Search for "15" returned 4954 results

63 min
goto fail;
exploring two decades of transport layer insecurity

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?
58 min
Script Your Car!
Using existing hardware platforms to integrate python into…

61 min
Dead Man Edition
Auf dem Weg zu fairer Elektronik am Beispiel der Elkos …

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
62 min
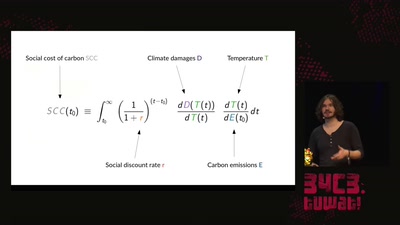
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

59 min
Security of the IC Backside
The future of IC analysis

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…
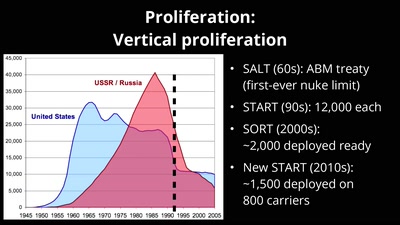
61 min
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

60 min
Quantum Cryptography
from key distribution to position-based cryptography

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

64 min