Search for "15" returned 4954 results

60 min
Crypto Wars Part II
The Empires Strike Back

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice
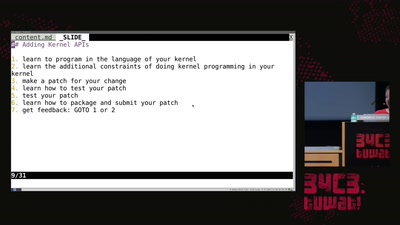
32 min
library operating systems
reject the default reality^W abstractions and substitute…

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

58 min
When hardware must „just work“
An inside look at x86 CPU design

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

59 min