Search for "42" returned 3647 results

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy

61 min
Warum die Digitale Revolution des Lernens gescheitert ist.
Fünf Desillusionen
62 min
SuperMUC-NG
… und das Rennen um den schnellsten Computer der Welt
62 min
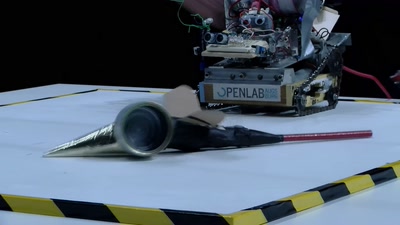
Space Hacker
Uploading rover...

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators
43 min
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

44 min
ASLR on the line
Practical cache attacks on the MMU
51 min
Haecksen gegen Cyberstalking
Ein Bericht vom Anti-Stalking Projekt

42 min
Code for Climate – Was 2020 bei Code for Germany passiert
Offene Daten können helfen, das Klima zu schützen.

57 min
Enterprise IT: Ein agiler Realitätsabgleich
Es gibt drei Arten von Lügen: Lügen, verdammte Lügen und…
54 min
"Day 2 Ops" Linux for Kubernetes and Container Workloads
Leveraging 10 years of Container Linux experience for…
42 min