Search for "30" returned 4245 results

62 min
Netzpolitik in der Schweiz 2016
Grundrechte per Volksentscheid versenken
42 min
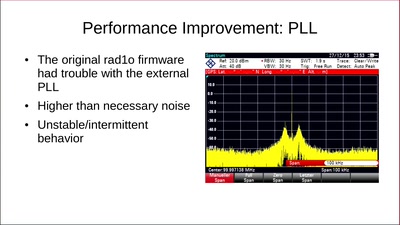
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…

45 min
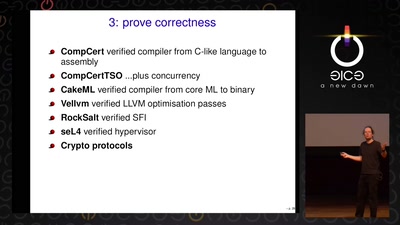
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

58 min
Funkzellenabfrage: Die alltägliche Rasterfahndung unserer Handydaten
Wie wir alle regelmäßig den Behörden ins Netz gehen und wie…

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

60 min
Tiger, Drucker und ein Mahnmal
Neues vom Zentrum für Politische Schönheit

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

61 min
Zamir Transnational Network und Zagreb Dairy
Das erste computer netzwerk in Krieg (Jugoslavia 1992-1997)

49 min