Search for "26" returned 4163 results

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

6 min
Chaotischer Catalysator Stipendien
Was ist das? Wie bewerbe ich mich?

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

13 min
OpenQA - review jobs and file bug report
OpenSUSE job review/bug report
41 min
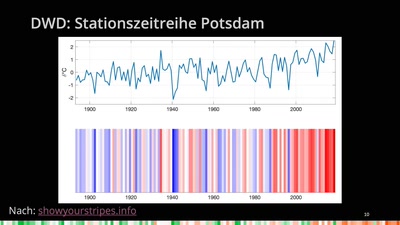
Nutzung öffentlicher Klimadaten
Früher war mehr Schnee

63 min
Dissecting HDMI
Developing open, FPGA-based capture hardware for conference…

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

58 min
Schweiz: Netzpolitik zwischen Bodensee und Matterhorn
E-ID, E-Voting, Netzsperren und andere netzpolitische…
35 min
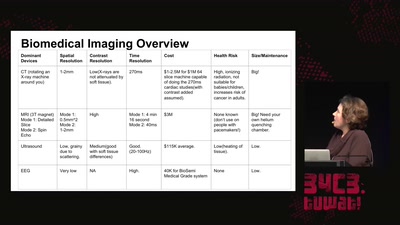
Low Cost Non-Invasive Biomedical Imaging
An Open Electrical Impedance Tomography Project
31 min
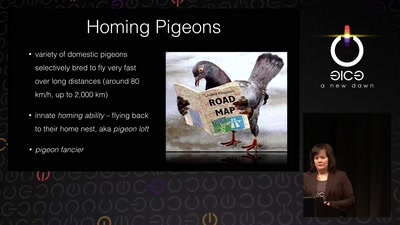
Living Drones
From war pigeons in 1914 to cyborg moths in 2014

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene
31 min
Media Disruption Led By The Blind
Hacking Visual Culture

42 min