Search for "15" returned 4793 results

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…
33 min
Computer Science in the DPRK
A view into technology on the other side of the world
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…
59 min
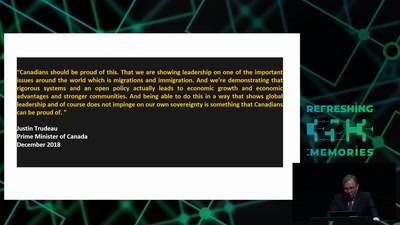
The Surveillance State limited by acts of courage and conscience
An update on the fate of the Snowden Refugees
30 min
“Nabovarme” opensource heating infrastructure in Christiania
Freetown Christiania´s digitally controlled/surveyed…

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

60 min
Hacking Reality
Mixed Reality and multi-sensory communication

62 min
To Protect And Infect, Part 2
The militarization of the Internet

43 min
Repair-Cafés
… und warum ihr dabei mitmachen solltet
32 min
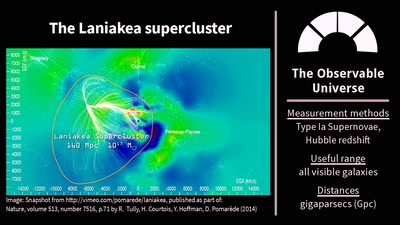
The Universe Is, Like, Seriously Huge
Stuff in Space Is Far Away – but How Do We Know?
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…
35 min
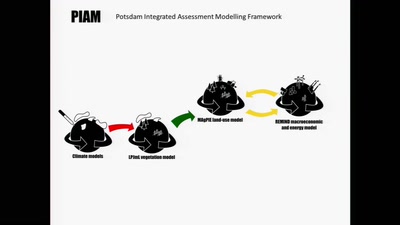
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…

62 min
„Wir beteiligen uns aktiv an den Diskussionen“
Die digitale „Agenda“ der Bundesregierung aus inhaltlicher,…

62 min
Was schützt eigentlich der Datenschutz?
Warum DatenschützerInnen aufhören müssen von individueller…

31 min
TrustZone is not enough
Hijacking debug components for embedded security

65 min