Search for "20" returned 4812 results

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…

43 min
This is NOT a proposal about mass surveillance!
Analysing the terminology of the UK’s Snooper’s Charter

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything
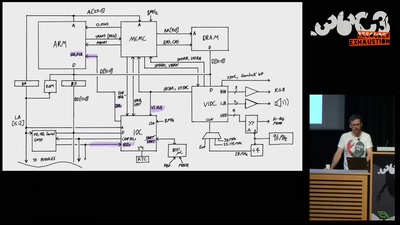
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

61 min
Beeinflussung durch Künstliche Intelligenz
Über die Banalität der Beeinflussung und das Leben mit…
61 min
Trügerische Sicherheit
Wie die Überwachung unsere Sicherheit gefährdet

60 min
Quantum Cryptography
from key distribution to position-based cryptography
63 min
Das Assange-Auslieferungsverfahren
Als Prozessbeobachter in London

90 min
Security Nightmares
Damit Sie auch morgen schlecht von Ihrem Computer träumen.…
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

54 min