Search for "31" returned 4036 results

26 min
Opening Event
35C3: Refreshing Memories

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

59 min
Security of the IC Backside
The future of IC analysis

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom

60 min
Quantum Cryptography
from key distribution to position-based cryptography
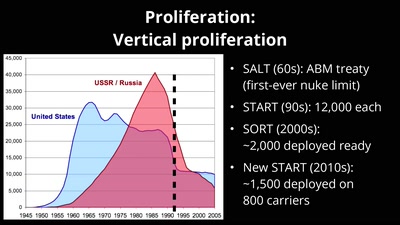
61 min
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

33 min
Turing Complete User
What can be done to protect the term, the notion and the…

25 min
»Hard Drive Punch«
Destroying data as a performative act
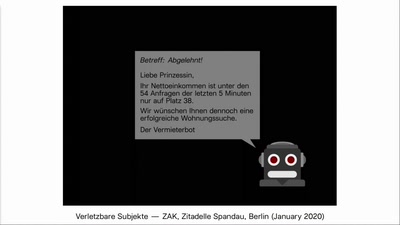
40 min
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…
32 min
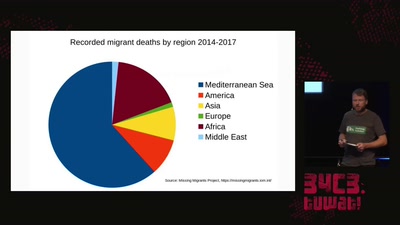
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution

29 min
Perfect Paul
On Freedom of Facial Expression
61 min