Search for "25" returned 4410 results

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

33 min
Turing Complete User
What can be done to protect the term, the notion and the…

34 min
Ling - High level system programming
modular and precise resource management

60 min
Beyond your cable modem
How not to do DOCSIS networks
35 min
Understanding millions of gates
Introduction to IC reverse engineering for…

59 min
Financial surveillance
Exposing the global banking watchlist
66 min
31C3 Keynote
A New Dawn

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques

58 min
Wie klimafreundlich ist Software?
Einblicke in die Forschung und Ausblick in die…
38 min
Policing the Romantic Crowd
Velocipedes and Face Recognition

41 min
Die Häuser denen, die darin wohnen!
Langfristig bezahlbares, gemeinsames „Mieteigentum“…

61 min
Computational Meta-Psychology
An Artificial Intelligence exploration into the creation of…

58 min
Switches Get Stitches
Industrial System Ownership

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

30 min
Privacy and Consumer Markets
Reversing the Surveillance Business Model
33 min
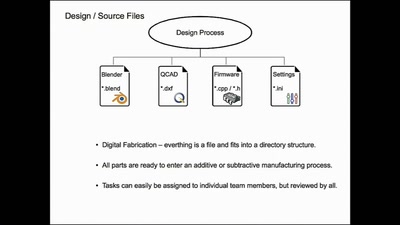
Structuring open hardware projects
experiences from the “i3 Berlin” 3D printer project with…

45 min