Search for "11" returned 4570 results

61 min
Net Neutrality in Europe
alea iacta est
61 min
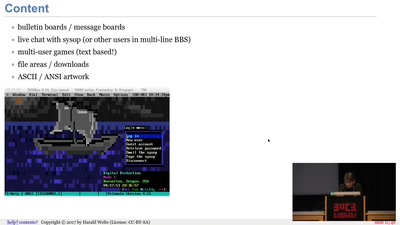
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

30 min
Privacy and Consumer Markets
Reversing the Surveillance Business Model

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

59 min
Financial surveillance
Exposing the global banking watchlist

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice
60 min
Katastrophe und Kommunikation am Beispiel Nord-Ost-Syrien
Humanitäre Hilfe zwischen Propaganda, Information und…

70 min
Security Nightmares 0x14
Was Sie schon immer nicht über darüber wissen wollten wer…

58 min
Wie klimafreundlich ist Software?
Einblicke in die Forschung und Ausblick in die…

77 min
Feminist Perspectives
Inclusive and Diverse Spaces and Communities

58 min
Switches Get Stitches
Industrial System Ownership

45 min
To Protect And Infect
The militarization of the Internet

43 min