Search for "54" returned 3273 results

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…

58 min
PLC-Blaster
Ein Computerwurm für PLCs

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min
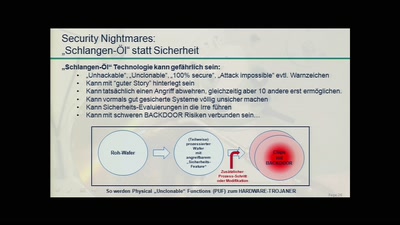
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy
45 min
Patente töten.
Wie Politik und Pharma den gerechten Zugang zum Impfstoff…
56 min
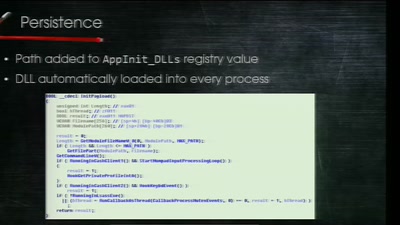
Electronic Bank Robberies
Stealing Money from ATMs with Malware

58 min
Schweiz: Netzpolitik zwischen Bodensee und Matterhorn
E-ID, E-Voting, Netzsperren und andere netzpolitische…
60 min
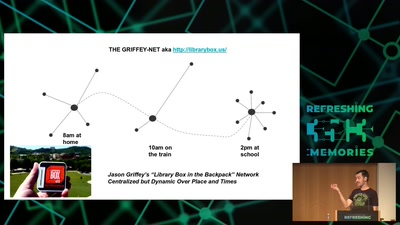
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…
61 min
25 Jahre Chipkarten-Angriffe
Von der Historie zur Zukunft

57 min
Theater und Quantenzeitalter
„Die Parallelwelt“- Das Schauspiel Dortmund und die…
40 min