Search for "13" returned 4960 results
33 min
The Transhumanist Paradox
Deciding between technological utopias in a liberal state
30 min
Mietshäusersyndikat: den Immobilienmarkt hacken
Wie man ein Haus kaufen kann ohne es zu besitzen

30 min
Syrian Archive
Preserving documentation of human rights violations
31 min
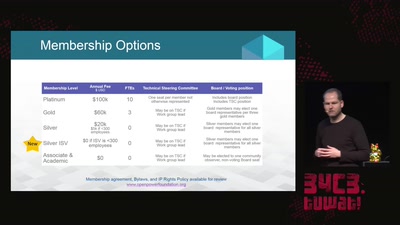
openPower - the current state of commercial openness in CPU development
is there no such thing as open hardware?

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?

58 min
Switches Get Stitches
Industrial System Ownership

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution
31 min
DPRK Consumer Technology
Facts to fight lore

113 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 33C3

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…
55 min
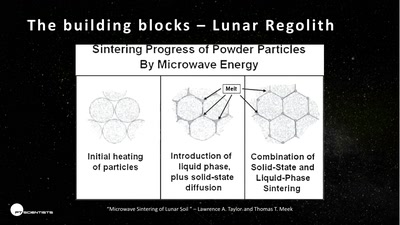
3D printing on the moon
The future of space exploration
67 min
Mit Kunst die Gesellschaft hacken
Das Zentrum für politische Schönheit

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

41 min
Österreich: Überwachungsstaat oder doch nur Digitalisierung für Anfänger?
Ein Jahr unter der rechtsextremen Regierung

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

61 min