Search for "28" returned 4411 results
55 min
3D printing on the moon
The future of space exploration

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

51 min
How to contribute to make open hardware happen
Mooltipass, Openpandora/Pyra and Novena/Senoko: how I…

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

67 min
The Maker movement meets patent law
How many windows are open in the patent fortress

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…
60 min
Die verborgene Seite des Mobilfunks
HF-Störquellen im Uplink
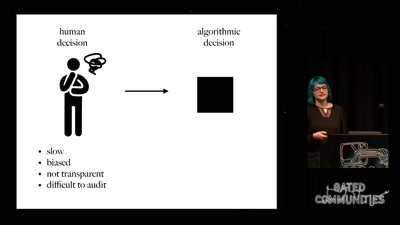
60 min
Prediction and Control
Watching Algorithms

68 min
#afdwegbassen: Protest, (Club-)Kultur und antifaschistischer Widerstand
Über kreative Organisation, poltische Aktionen und das…

61 min
Computational Meta-Psychology
An Artificial Intelligence exploration into the creation of…
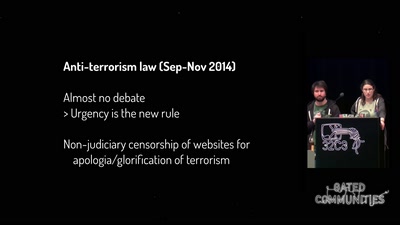
27 min
One year of securitarian drift in France
From the Bill on Intelligence to the State of Emergency

26 min
Technomonopolies
How technology is used to subvert and circumvent…

56 min
Planes and Ships and Saving Lives
How soft and hardware can play a key role in saving lives…

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP

60 min