Search for "28" returned 4396 results

115 min
Hacker Jeopardy
Zahlenraten für Geeks
56 min
Electronic Bank Robberies
Stealing Money from ATMs with Malware

58 min
Uncertain Concern
How Undocumented Immigrants in the US Navigate Technology

59 min
Provable Security
How I learned to stop worrying and love the backdoor

32 min
Relativitätstheorie für blutige Anfänger
Raum, Zeit, Licht und Gravitation, wie hängt das zusammen?
99 min
Fnord-Jahresrückblick
Wir helfen euch, die Fnords zu sehen!
62 min
Die Affäre Hannibal
Eine erste Bilanz

107 min
Nougatbytes 11₂
Die geekige Wort- & Bilderrätselspielshau ist zuЯück
41 min
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

62 min
SymbiFlow - Finally the GCC of FPGAs!
A fully FOSS, Verilog to bitstream, timing driven, cross…

72 min
Console Hacking
Breaking the 3DS
60 min
Simulating Universes
What Virtual Universes Can Tell Us About Our Own

59 min
How to teach programming to your loved ones
Enabling students over example-driven teaching

40 min
Radical Digital Painting
Fantastic Media Manipulation
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy
35 min
YOUR DATA MIRROR
Wie die Macht der Daten die Demokratie untergräbt
53 min
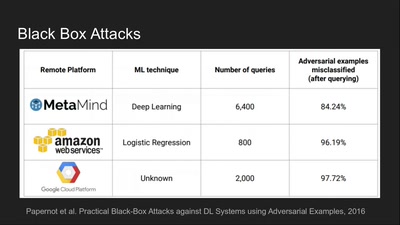
Deep Learning Blindspots
Tools for Fooling the "Black Box"
59 min
NSA Points of Presence in AT
Vortrag mit aktuellen Fotos aus luftigen Perspektiven

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

59 min