Search for "12" returned 5156 results

57 min
Kryptographie nach Snowden
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min
Lets break modern binary code obfuscation
A semantics based approach

55 min
3D Casting Aluminum
Too Much Fun with Microwaves

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy
60 min
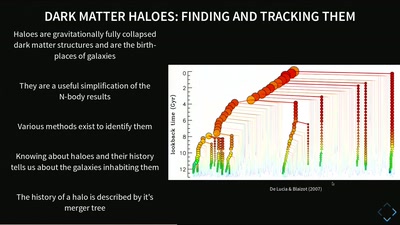
Simulating Universes
What Virtual Universes Can Tell Us About Our Own

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.
60 min
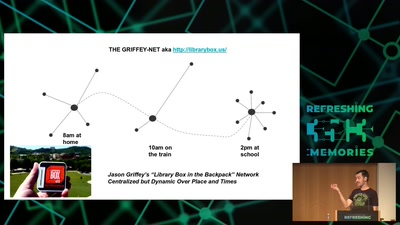
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

55 min
White-Box Cryptography
Survey
58 min
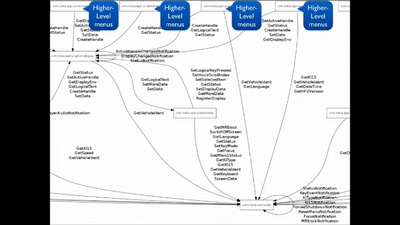
Script Your Car!
Using existing hardware platforms to integrate python into…

58 min
Überwachen und Sprache
How to do things with words

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

64 min