Search for "18" returned 4783 results

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…

59 min
Security of the IC Backside
The future of IC analysis

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
61 min
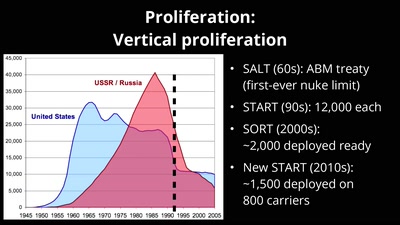
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

60 min
Quantum Cryptography
from key distribution to position-based cryptography
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice
61 min
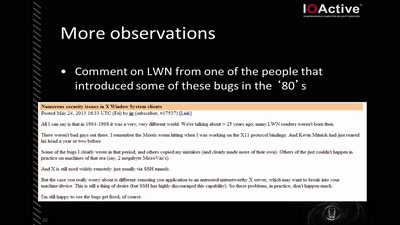
X Security
It's worse than it looks

90 min