Search for "18" returned 4654 results

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist

42 min
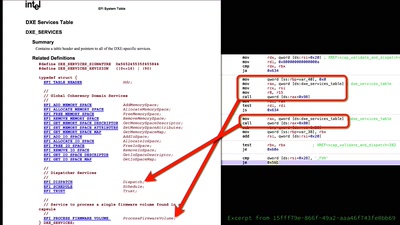
Firmware Fat Camp
Embedded Security Using Binary Autotomy

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…

58 min
Virtual Machine Introspection
From the Outside Looking In
62 min
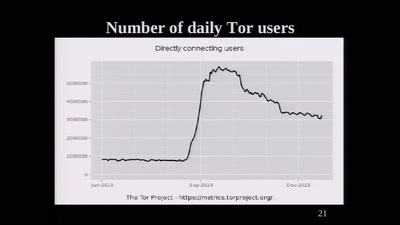
The Tor Network
We're living in interesting times

58 min
Die Krise der Bilder ist die Krise der Politik
Die Krise der Politik ist die Krise der Bilder

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap
54 min
Der Kampf um Netzneutralität
Wer kontrolliert das Netz?

55 min
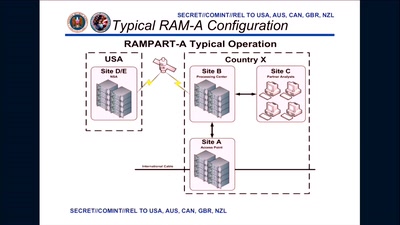
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.
58 min
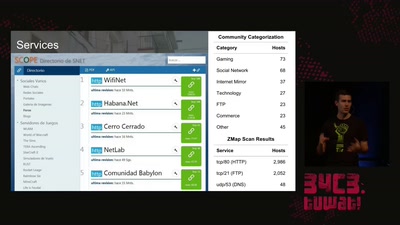
The Internet in Cuba: A Story of Community Resilience
Get a unique tour of some of the world’s most unusual…

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs

58 min
Glitching For n00bs
A Journey to Coax Out Chips' Inner Secrets
64 min