Popular Events
All - 2026 - 2025 - 2024 - 2023 - 2022 - 2021 - 2020 - 2019 - 2018 - 2017 - 2016 - 2015 - 2014 - 2013 - 2012 - 2011 - 2010 - 2009 - 2008 - 2007 - 2006 - 2005 - 2004 - 2003 - 2002 - 2001 - 2000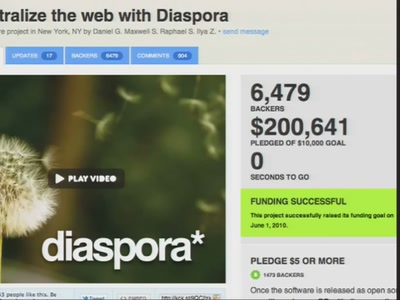
47 min
Wie finanziere ich eine Mondmission?
Von Würstchen verkaufen bis Ballonflüge – ein…

63 min
Power gadgets with your own electricity
escape the basement and make the sun work for you
77 min
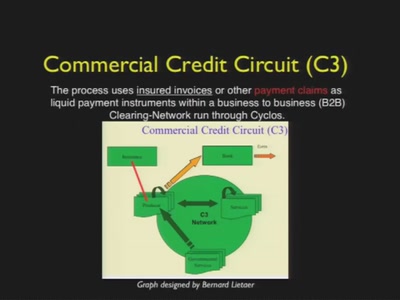
Imagine the Future of Money
Economic transformations, hacker culture and why we should…
51 min
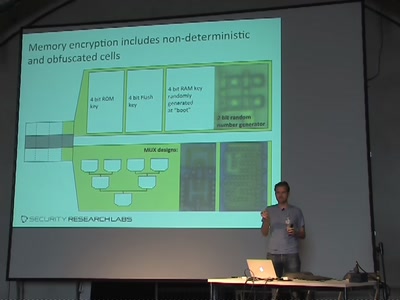
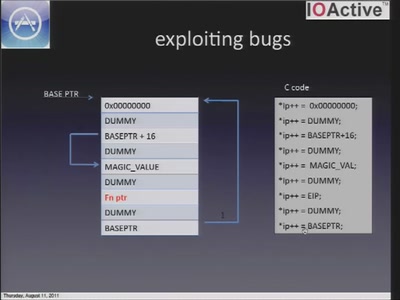
iOS application security
A look at the security of 3rd party iOS applications
51 min
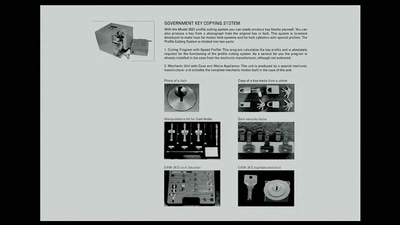
BuggedPlanet
Surveillance Industry & Country's Actings

65 min
Quantified-Self and OpenBCI Neurofeedback Mind-Hacking
Transhumanism, Self-Optimization and Neurofeedback for…
66 min
KinectFusion
Real-time 3D Reconstruction and Interaction Using a Moving…

25 min
Security Log Visualization with a Correlation Engine
What's inside your network?

64 min
What is in a name?
Identity-Regimes from 1500 to the 2000s

56 min
Rootkits in your Web application
Achieving a permanent stealthy compromise of user accounts…

63 min
She-Hackers: Millennials and Gender in European F/LOSS Subcultures
A Presentation of Research and Invitation for Debate
28 min