58 min
How to Destroy a Laptop with Top Secrets
How did GCHQ do it to the Guardian's copy of Snowden's…

31 min
Update: Vor Windows10 Update Warnung
Update (Patch) Debakel
55 min
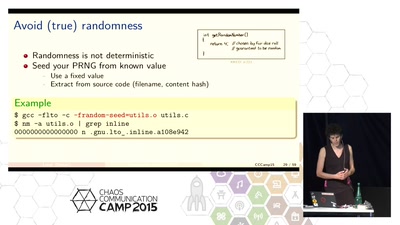
How to make your software build reproducibly
Get a verifiable path from source to binary
46 min
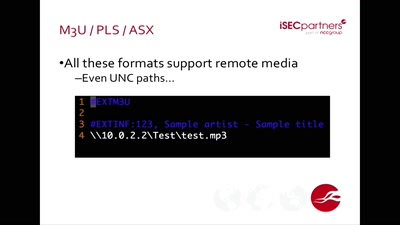
Bugged Files
Is Your Document Telling on You?
48 min
Advanced interconnect attacks
Chasing GRX and SS7 vulns
28 min
Hardware attacks: hacking chips on the (very) cheap
How to retrieve secret keys without going bankrupt

30 min
Privacy Badger
Stop being tracked online
42 min
Let's Encrypt
A Certificate Authority To Encrypt the Entire Web

29 min
Jumping the Paywall
How to freely share research without being arrested
52 min
TLS interception considered harmful
How Man-in-the-Middle filtering solutions harm the security…
56 min