75 min
Tracker fahrn
We Track Harder - We Track More! Take the pain out of…

42 min
Inside the Mac OS X Kernel
Debunking Mac OS Myths

34 min
Playstation Portable Cracking
How In The End We Got It All!

56 min
Desperate House-Hackers
How to Hack the Pfandsystem
90 min
Security Nightmares 2008
Oder: worüber wir nächstes Jahr lachen werden
59 min
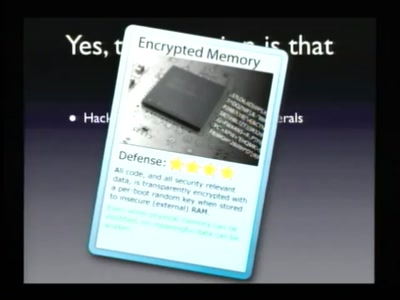
Why Silicon-Based Security is still that hard: Deconstructing Xbox 360 Security
Console Hacking 2007

57 min
C64-DTV Hacking
Revisiting the legendary computer in a joystick

57 min
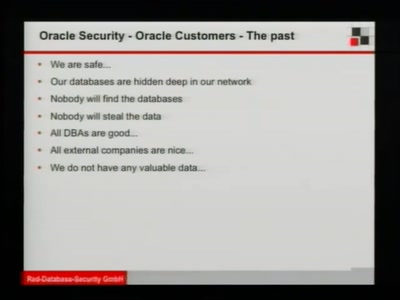
Hacking SCADA
how to own critical infrastructures

59 min
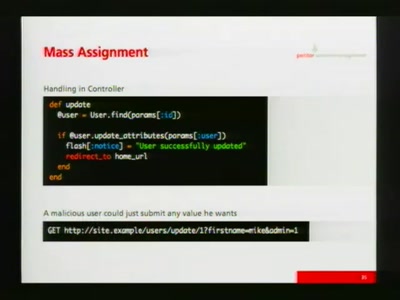
Grundlagen der sicheren Programmierung
Typische Sicherheitslücken

63 min
Wireless Kernel Tweaking
or how B.A.T.M.A.N. learned to fly

59 min
10GE monitoring live!
How to find that special one out of millions
53 min
Crouching Powerpoint, Hidden Trojan
An analysis of targeted attacks from 2005 to 2007

44 min
Port Scanning improved
New ideas for old practices
50 min
To be or I2P
An introduction into anonymous communication with I2P

42 min
Just in Time compilers - breaking a VM
Practical VM exploiting based on CACAO

45 min
OpenSER SIP Server
VoIP-Systeme mit OpenSER

46 min
A collection of random things
Look what I found under the carpet
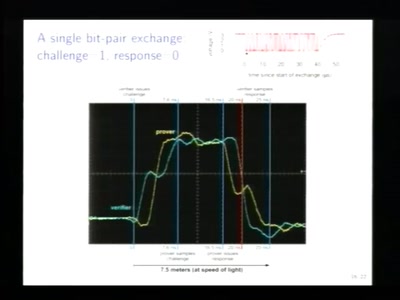
62 min
Relay attacks on card payment: vulnerabilities and defences
Keeping your enemies close

58 min
Cybercrime 2.0
Storm Worm

42 min
From Ring Zero to UID Zero
A couple of stories about kernel exploiting
48 min
One Token to Rule Them All
Post-Exploitation Fun in Windows Environments
44 min
Unusual Web Bugs
A Web Hacker's Bag O' Tricks

52 min