Search for "Ike" returned 2789 results

36 min
Modchips of the State
Hardware implants in the supply-chain

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics
42 min
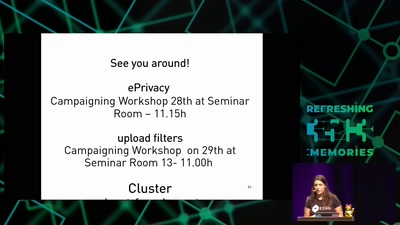
Citzens or subjects? The battle to control our bodies, speech and communications
A call to action to defend our ePrivacy and eliminate…

63 min
goto fail;
exploring two decades of transport layer insecurity

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.

54 min
What Price the Upload Filter?
The history and costs of government exceptional access

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

32 min
Visceral Systems
Approaches to working with sound and network data…

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

63 min
Through a PRISM, Darkly
Everything we know about NSA spying

58 min
Baseband Exploitation in 2013
Hexagon challenges

60 min