Search for "245" returned 2281 results

58 min
When hardware must „just work“
An inside look at x86 CPU design

55 min
White-Box Cryptography
Survey

58 min
Baseband Exploitation in 2013
Hexagon challenges

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

63 min
Through a PRISM, Darkly
Everything we know about NSA spying

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?
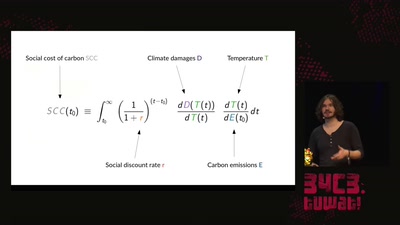
62 min
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

63 min
goto fail;
exploring two decades of transport layer insecurity

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

61 min