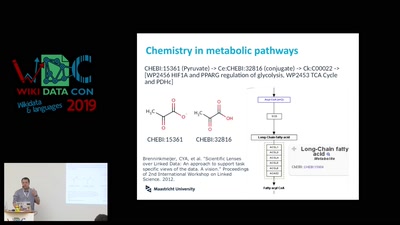
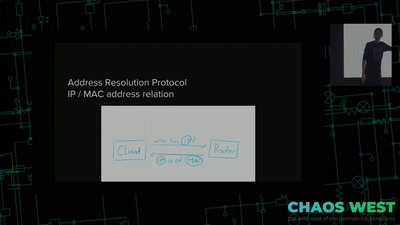
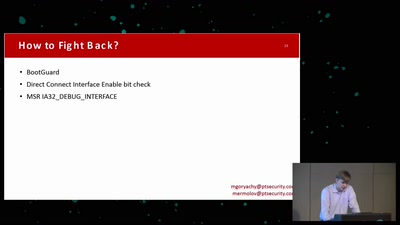
Search for "ilf" returned 2569 results

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study

32 min
Verified Firewall Ruleset Verification
Math, Functional Programming, Theorem Proving, and an…
61 min
Avoiding kernel panic: Europe’s biggest fails in digital policy-making
How the institutions fuck up, and how we fuck it up as well
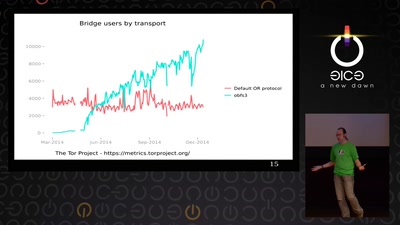
72 min
State of the Onion
Neuland

53 min
Console Hacking 2016
PS4: PC Master Race
37 min
Listening Back Browser Add-On Tranlates Cookies Into Sound
The Sound of Surveillance

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

33 min
Retail Surveillance / Retail Countersurveillance
50 most unwanted retail surveillance technologies / 50 most…
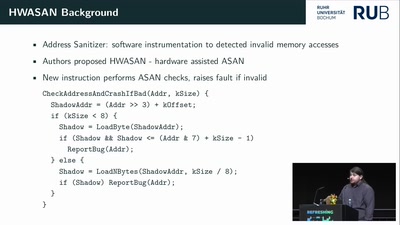
37 min