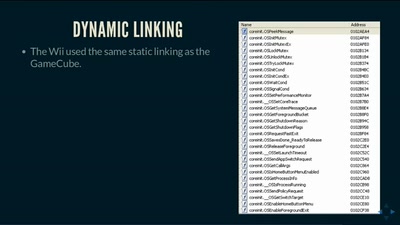
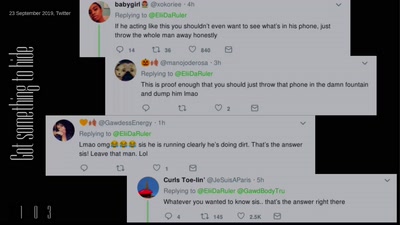
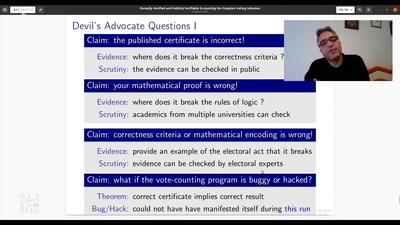
Search for "eDxt" returned 202 results

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

55 min
Attribution revolution
Turning copyright upside-down with metadata

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy
56 min
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform
95 min